Executive Summary:
This report documents confirmed exploitation of 2025 CVEs by nation-state APT groups and cybercriminal collectives. Only incidents with publicly verifiable sources are included. Each section provides the exploited CVE, threat actor attribution, campaign context, and a simplified exploit sketch
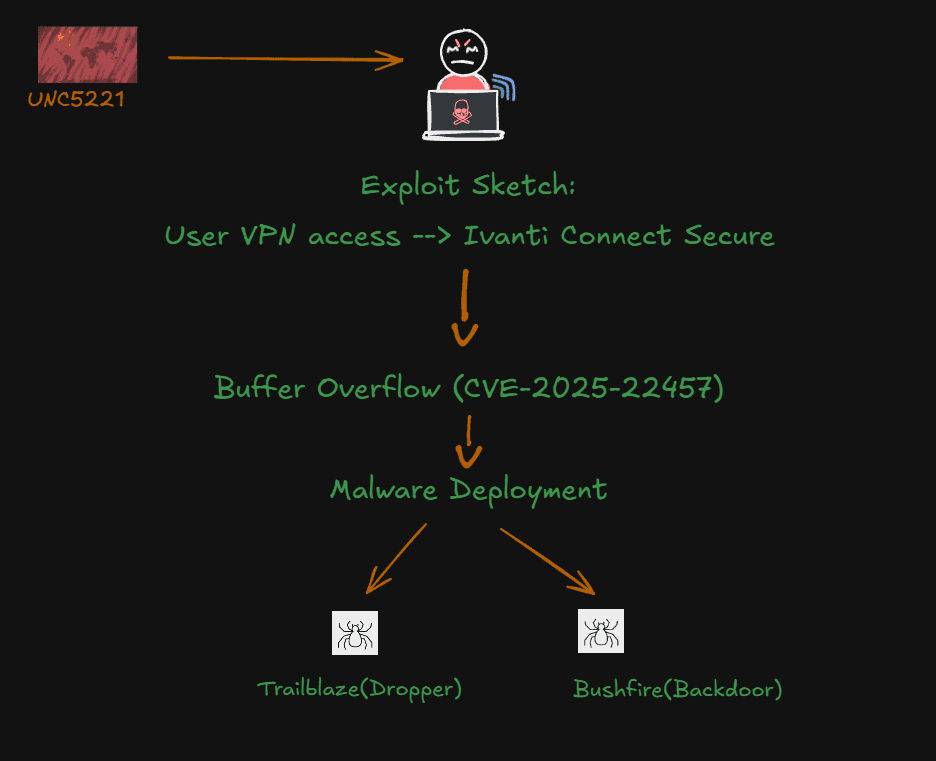
1. UNC5221 – CVE-2025-22457

• Vulnerability: Buffer overflow in Ivanti Connect Secure VPN
• Campaign: Deployment of TRAILBLAZE and BUSHFIRE malware in targeted espionage ops.
• Victim Sectors: Government, Finance
CVE-Explanation:
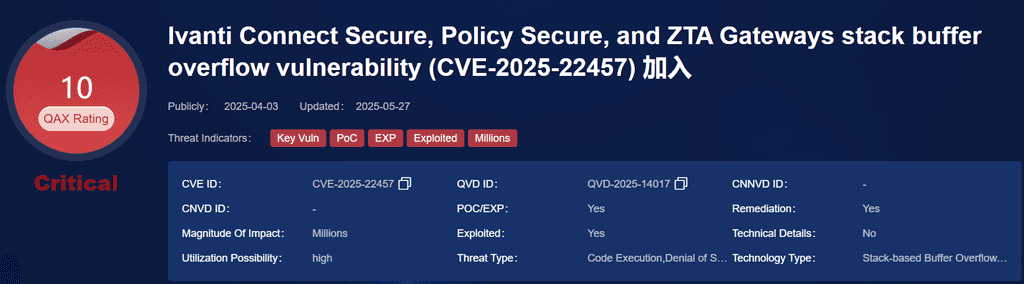
This vulnerability in Ivanti Connect Secure, Policy Secure, and ZTA Gateways that may allow remote code execution and denial of service. Caused by a stack buffer overflow from improper input validation, the flaw lets unauthenticated attackers remotely execute code or disrupt services. Successful exploitation could grant full control of the system or render it unavailable, posing a serious threat to system integrity and availability.
Exploit Sketch:
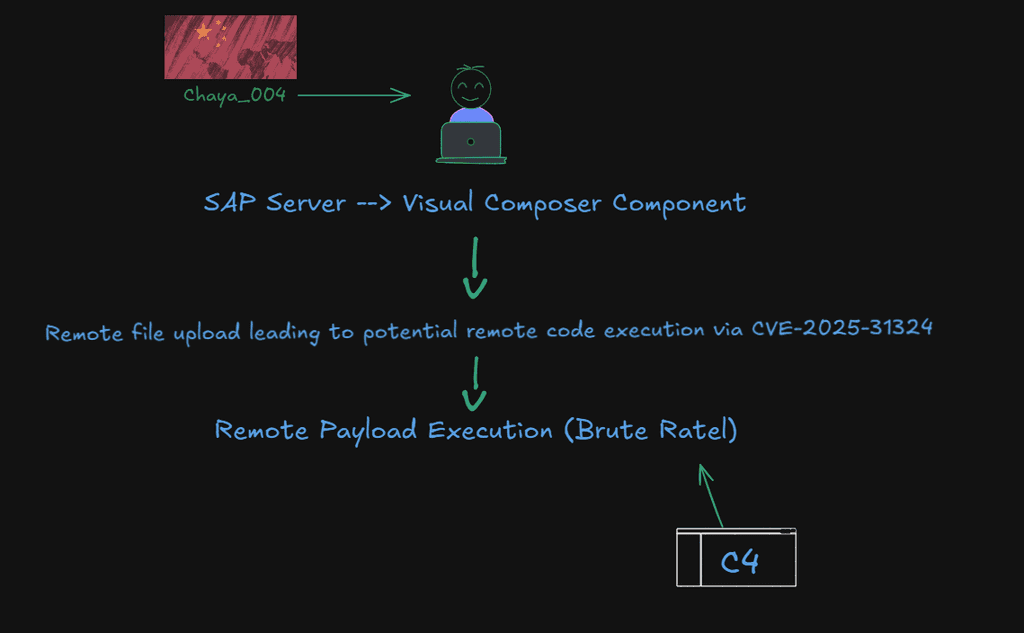
2. Chaya_004 – CVE-2025-31324

• Vulnerability: RCE in SAP NetWeaver Visual Composer
• Campaign: Brute Ratel deployment to compromise ERP systems
• Victim Sectors: Manufacturing, Energy
CVE-Explanation:
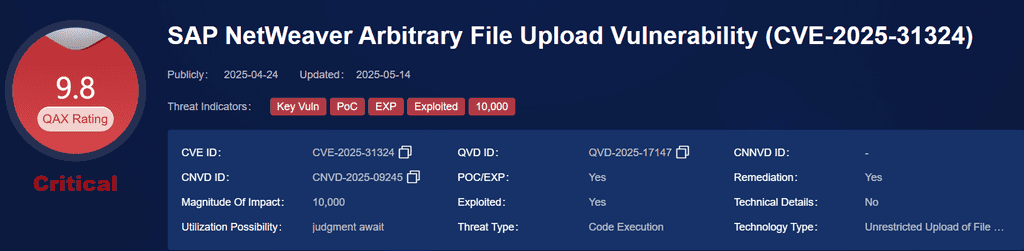
This vulnerability in SAP NetWeaver Visual Composer Metadata Uploader that enables unauthenticated file upload and remote code execution. Attackers can upload and execute malicious binaries, gaining unauthorized access, executing code, and stealing sensitive data. Exploitation may lead to full system compromise and data leakage, making this vulnerability a critical threat requiring immediate attention and patching.
Exploit Sketch:
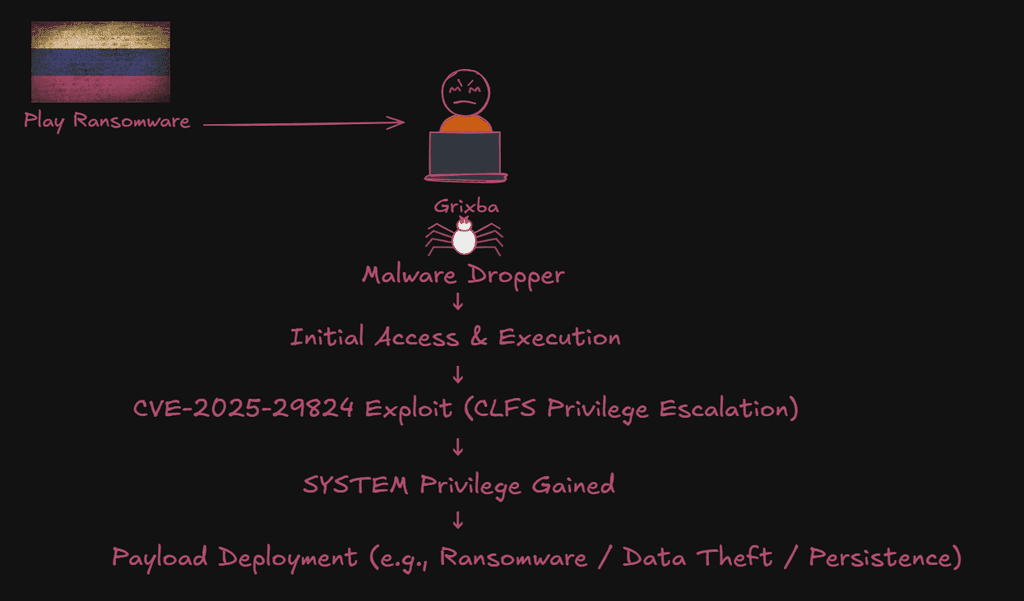
3. Play Ransomware Group – CVE-2025-29824

• Vulnerability: Windows CLFS Privilege Escalation
• Campaign: Grixba malware deployment followed by Play ransomware
• Victim Sectors: Healthcare, Telecom
CVE-Explanation:
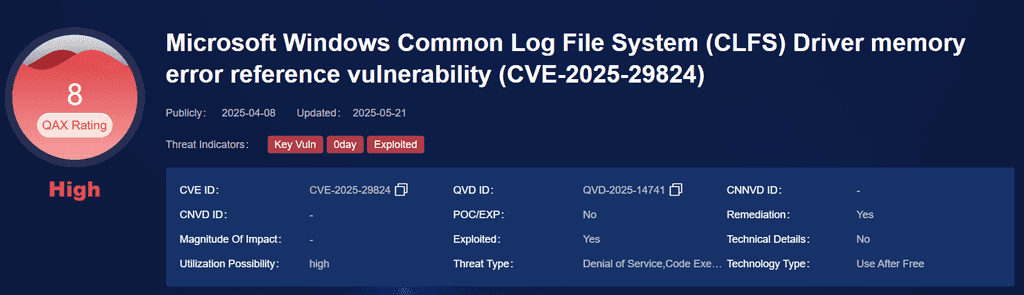
This vulnerability in Microsoft Windows Common Log File System (CLFS) Driver that may lead to local privilege escalation. Attackers can exploit it to gain elevated privileges, execute malicious code, or cause denial of service. Successful exploitation could result in full system control, crashes, or data leakage, posing a critical threat to system stability and confidentiality. Prompt patching is essential to mitigate this risk.
Exploit Sketch:
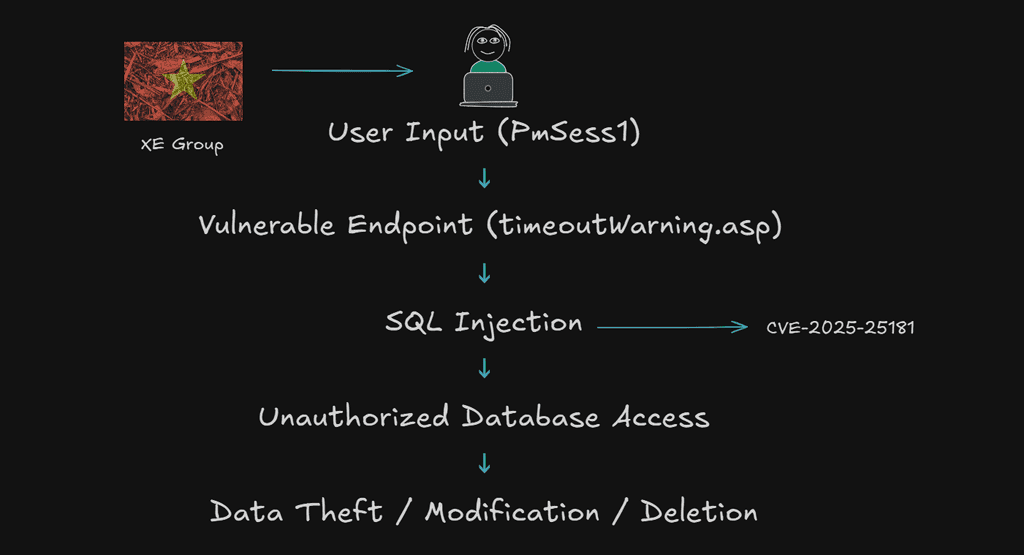
4. XE Group – CVE-2025-25181

• Vulnerability: SQL Injection in VeraCore Fulfillment System
• Campaign: ASPXSpy web shell deployment for financial data theft
• Victim Sectors: E-commerce, Logistics
CVE-Explanation:
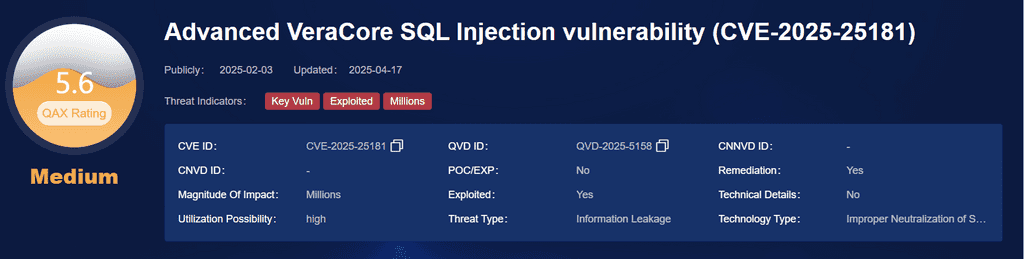
This vulnerability in Advantive VeraCore that enables SQL injection via the PmSess1 parameter in timeoutWarning.asp. Attackers can exploit it to execute malicious SQL commands, potentially leading to data theft, modification, or deletion. This poses a significant risk to data confidentiality and integrity. Immediate remediation is critical to prevent unauthorized access and sensitive data leakage.
Exploit Sketch:
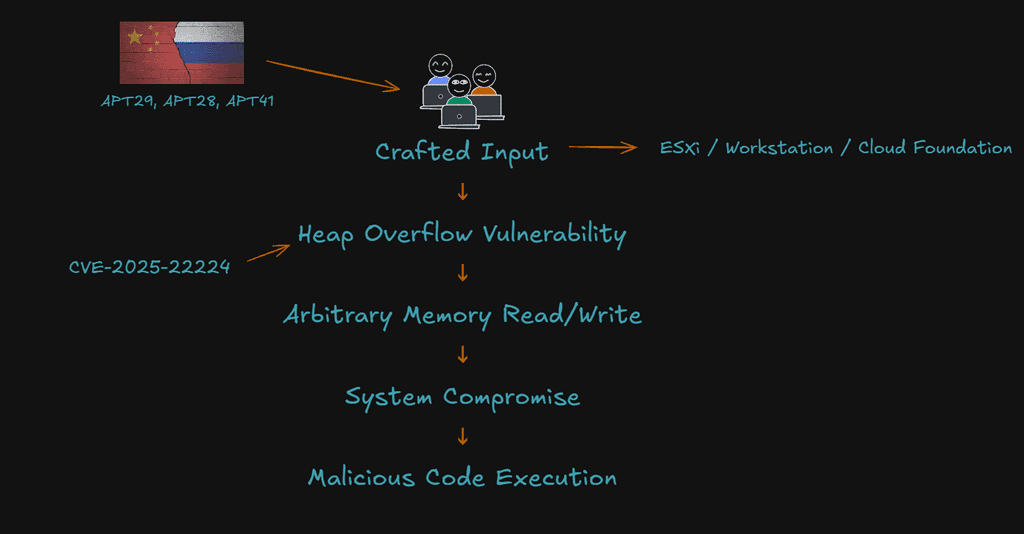
5. APT29, APT28, APT41 – CVE-2025-22224

• Vulnerability: VMware ESXi privilege escalation vulnerability
• Campaign: Cross-sector espionage operations exploiting virtualized environments
• Victim Sectors: Diplomacy, Defense, Energy
CVE-Explanation:
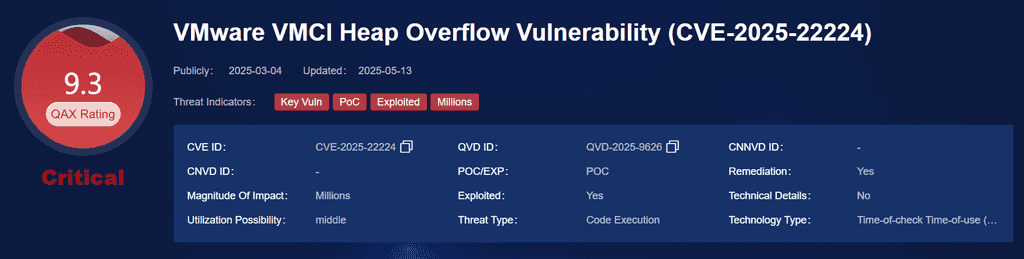
This vulnerability in VMware ESXi, Workstation, and Cloud Foundation that allows arbitrary memory read and write through a heap overflow flaw. Attackers can exploit this to compromise system memory, potentially leading to full system control. Successful exploitation may enable malicious code execution, posing severe risks to system integrity, confidentiality, and availability. Prompt patching and monitoring are essential to mitigate this threat.
Exploit Sketch:
Conclusion:
This report highlights zero-day exploits actively leveraged by APT groups from early 2025 to present, detailing associated CVEs, attack campaigns, and exploit workflows. Each threat actor profiled has weaponized a 2025 vulnerability in live operations, targeting critical infrastructure, enterprise environments, and government entities.
References:
• TechRadar Pro, Kudelski Security • Help Net Security, Hacking Reviews • Alpha Hunt Blog